ಟ್ವೀಟ್ಗಳು
- ಟ್ವೀಟ್ಗಳು
- ಟ್ವೀಟ್ಗಳು & ಪ್ರತಿಕ್ರಿಯೆಗಳು
- ಮಾಧ್ಯಮ
@we1x ತಡೆಹಿಡಿಯಲಾಗಿದೆ
ನೀವು ಖಚಿತವಾಗಿಯೂ ಈ ಟ್ವೀಟ್ಗಳನ್ನು ನೋಡಲು ಬಯಸುವಿರಾ? ಟ್ವೀಟ್ಗಳನ್ನು ನೋಡುವುದು @we1x ಅವರನ್ನು ತಡೆತೆರವುಗೊಳಿಸುವುದಿಲ್ಲ.
-
ಪಿನ್ ಮಾಡಿದ ಟ್ವೀಟ್
CSP-Evaluator (http://csp-evaluator.withgoogle.com ) got released today! Find out if your
#CSP is among the 95% that can be trivially bypassed!pic.twitter.com/PJzJ5BACao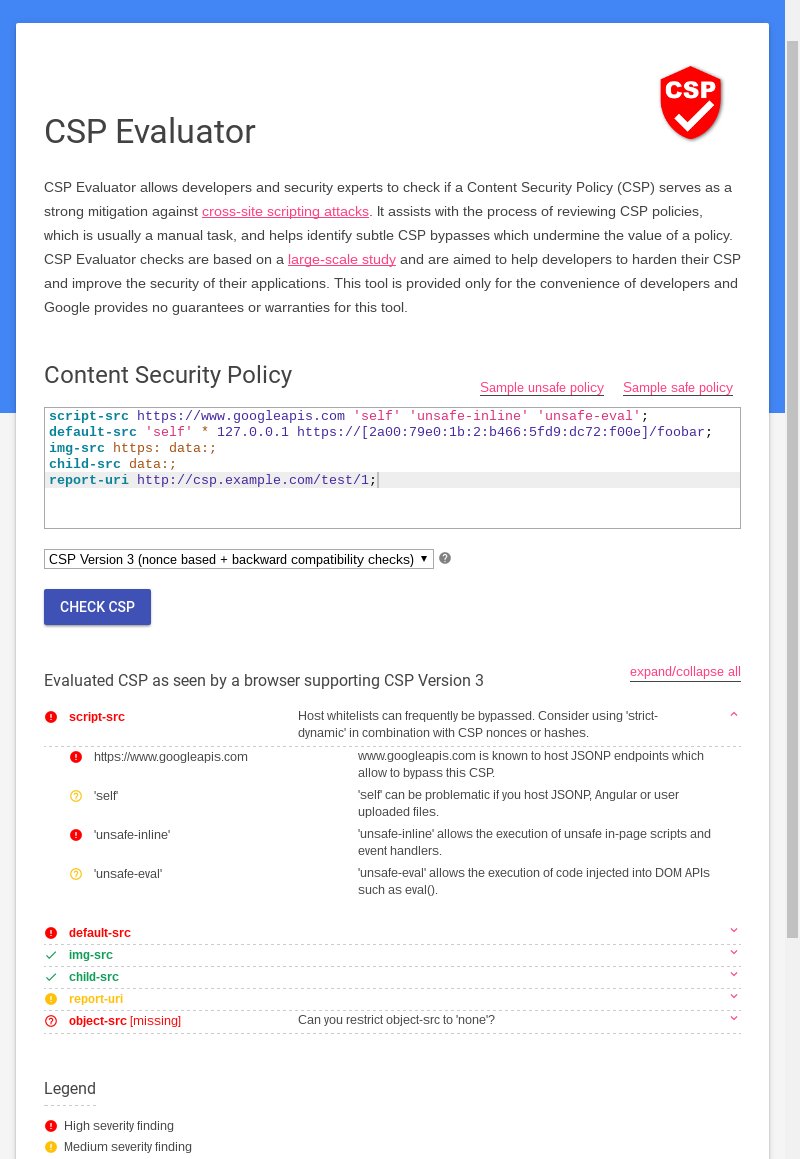
-
Wrote up a summary of some of the content security policy related work we have been up to on http://GitHub.com https://githubengineering.com/githubs-post-csp-journey/ …
-
Edge now fully supports
#CSP version 2 (incl. nonces).#strictdynamic is on their radar.https://blogs.windows.com/msedgedev/2017/01/10/edge-csp-2/#OJUpBuUwOoegJQYf.97 … -
Glad to present at
@ETH in Zürich "Breaking Bad Content Security Policies" with@we1x tomorrow, at 9:15, CAB G 61 – http://www.netsec.ethz.ch/education/courses/netsec-2016/ … -
Goodbye
#XSS! GAE Scaffold now supports Closure Templates (strict autoescape!) with auto-noncing and nonce-based#CSP with#strictdynamic.https://twitter.com/philames/status/802188284596076544 … -
Thx everyone for joining my
#CSP talk at#DeepSec You can read up everything about strict csp here: https://csp.withgoogle.com -
strict-dynamic support for
#CSP landed in Firefox (nightly now, stable in FF52)! Kudos to the FF team#strictdynamic https://bugzilla.mozilla.org/show_bug.cgi?id=1299483 … -
Our
#CSP (@mikispag@slekies@arturjanc) research paper just got published by@TheOfficialACM http://dl.acm.org/citation.cfm?id=2978363 … -
Join my +
@mikispag's#IEEESecdev tutorial on Adopting Strict Content Security Policy for XSS Protection -
Great work on CSP. Evaluation and defense proposal. by
@mikispag@slekies@we1x@arturjanc#CCS16@acm_ccspic.twitter.com/Jlo8KnI2GM

-
#CCS16 picked a particular nice place for dinner this year!pic.twitter.com/mtgwvcqPIL
-
list of common whitelisted CSP domains that allow to bypass CSP now available as json: https://github.com/google/csp-evaluator/tree/master/whitelist_bypasses/json …
@aprilmpls@Scott_Helmehttps://twitter.com/we1x/status/788379608521510912 … -
I just pushed our open source version of CSP-Evaluator to github. Feel free to reuse checks & whitelist bypass list!https://github.com/google/csp-evaluator …
-
We just released a blog post, docs and a couple of tools (Evaluator, Mitigator) to help adopting a secure
#CSPhttps://security.googleblog.com/2016/09/reshaping-web-defenses-with-strict.html … -
This is one of the most important web sec papers in recent history: https://static.googleusercontent.com/media/research.google.com/en//pubs/archive/45542.pdf … (section 3.4 is where the juicy bits are)
-
Most
#CSP offer no XSS protection and are based on whitelists(median 12)#strictdynamic helps http://goo.gl/H5r4ds pic.twitter.com/2Rk28ErkbJ
-
Our (
@we1x@slekies@arturjanc)#CSP paper is out. 95% bypassable, whitelisting is doomed,#strictdynamic helps. https://research.google.com/pubs/pub45542.html … -
Our (
@mikispag@slekies@arturjanc)#CSP research paper (ACM CSS) is public now. It's time to drop whitelists! https://research.google.com/pubs/pub45542.html … -
Want to learn how to adopt strict
#CSP? Drop by our (@we1x@mikispag@arturjanc) tutorial for#IEEESecDev in Boston organized by@ieeecybsi! -
Lukas Weichselbaum ಹಿಂಬಾಲಿಸಿದ್ದಾರೆ the grugq, Mathias Bynens, Egor Homakov and 70 others
-
@thegrugq
Security Researcher :: Cultural Attaché :: PGP http://pgp.mit.edu/pks/lookup?op=get&search=0xDB60C7B9BD531054 … :: Не верь, не бойся, не проси
-
@mathias
Web standards fanatic. JavaScript, HTML, CSS, HTTP, performance, security, Bash, Unicode, macOS.
-
ಲೋಡಿಂಗ್ ಸಮಯ ಸ್ವಲ್ಪ ತೆಗೆದುಕೊಳ್ಳುತ್ತಿರುವಂತೆನಿಸುತ್ತದೆ.
Twitter ಸಾಮರ್ಥ್ಯ ಮೀರಿರಬಹುದು ಅಥವಾ ಕ್ಷಣಿಕವಾದ ತೊಂದರೆಯನ್ನು ಅನುಭವಿಸುತ್ತಿರಬಹುದು. ಮತ್ತೆ ಪ್ರಯತ್ನಿಸಿ ಅಥವಾ ಹೆಚ್ಚಿನ ಮಾಹಿತಿಗೆ Twitter ಸ್ಥಿತಿಗೆ ಭೇಟಿ ನೀಡಿ.


 Lukas Weichselbaum
Lukas Weichselbaum
 Patrick Toomey
Patrick Toomey
 Michele Spagnuolo
Michele Spagnuolo
 Marco Balduzzi
Marco Balduzzi
 lcamtuf
lcamtuf

