-
Day 86: Updating IndieAuth Docs #100DaysOfIndieWeb
Beginning a slow project of updating the docs about the IndieAuth spec, today I started by updating a few pages on the wiki. Right now, most of the docs about IndieAuth (the spec), and how to use it, live across a variety of pages on the wiki, grouped together at https://indieweb.org/Category:IndieAuth.
My goal with the spec IndieAuth is to make it an extension of the OAuth 2.0 spec. It has always been based off of the OAuth 2.0 spec, but I've never written it up properly as an extension. It's always been just a series of how-to guides. Additionally, I had originally started by specifying all of the responses being form-encoded responses, whereas the OAuth 2.0 spec says all responses must be JSON format. I've been slowly converting my various apps that use IndieAuth to support both, based on the HTTP Accept header, although I haven't publicized this much yet.
Today's project was updating the existing IndieAuth documentation on the wiki to explicitly include the JSON versions as a valid response format.
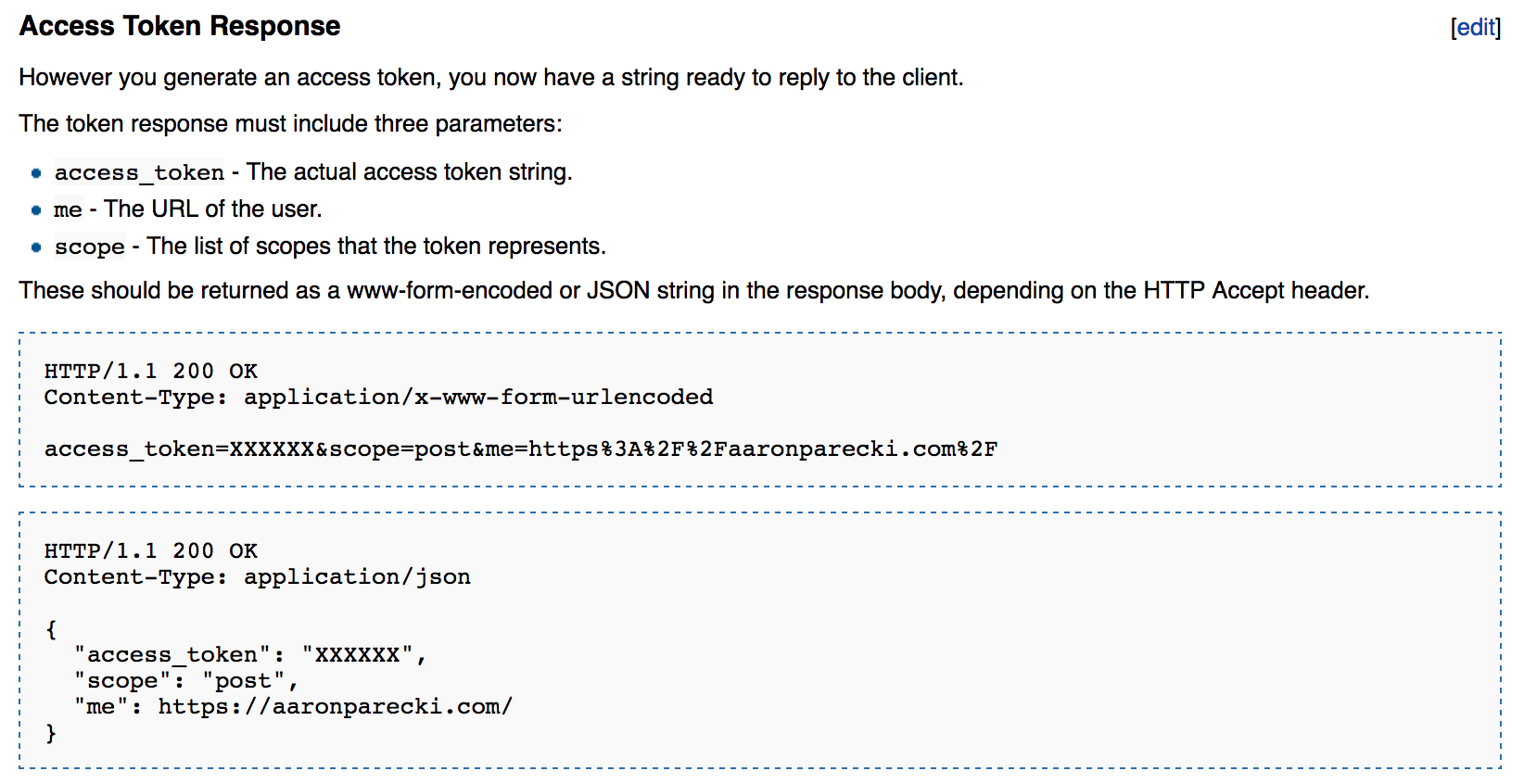
Eventually I hope to write up IndieAuth as a formal extension to OAuth 2.0, in the same format that something like the Device Flow is an extension.
-
Day 59: Updated the Logo on IndieAuth.com's GitHub Login #100DaysOfIndieWeb
This evening, Tantek pointed out to me that while he was logging in to the wiki via IndieAuth.com for the first time on a new computer, there was something a little strange about the IndieAuth.com flow...
Here's the screenshot of what he saw:
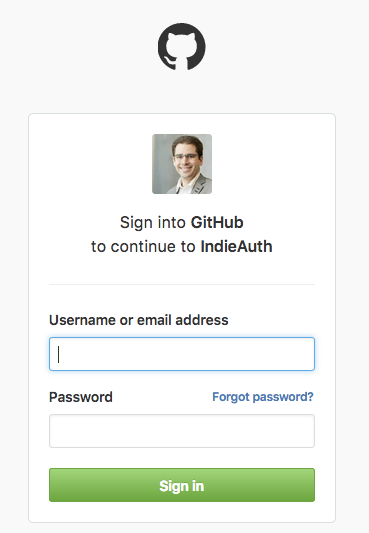
I definitely agree this is somewhat disconcerting. So here's what I did to fix it.
I first didn't realize that if you don't upload an application icon to GitHub when you create an application, it will use the profile photo of the user who created the application for the OAuth screen. I guess I should have remembered this, since I included a screenshot of GitHub's OAuth screen in the User Interface chapter of my OAuth book.
I first assumed that I would have to transfer the ownership the application to an organization that has the logo I wanted to appear. I did that, and encountered a strange message on GitHub when I moved the application from my aaronpk account to the new IndieAuth organization.
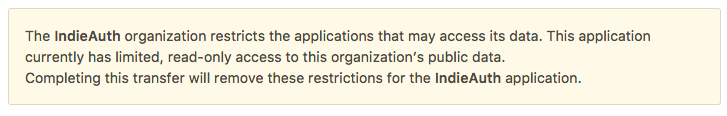
I have absolutely no idea what this message is trying to tell me. I reported my confusion to a friend who works at GitHub, so we'll see if they fix that soon.
Afterwards, I then realized I didn't in fact need to transfer the ownership of the application, and could just upload an application icon instead. Much easier!
So I uploaded a logo to GitHub, and also changed the name of the application from "IndieAuth" to "IndieAuth.com". This is part of my long-standing regret of naming this service IndieAuth, since it's also now a protocol that anyone can implement and is not actually tied to me running this service. I wish I could change the name of this service, but too many people are referencing indieauth.com in their code now, especially since it's one of the few remaining OpenID providers left.
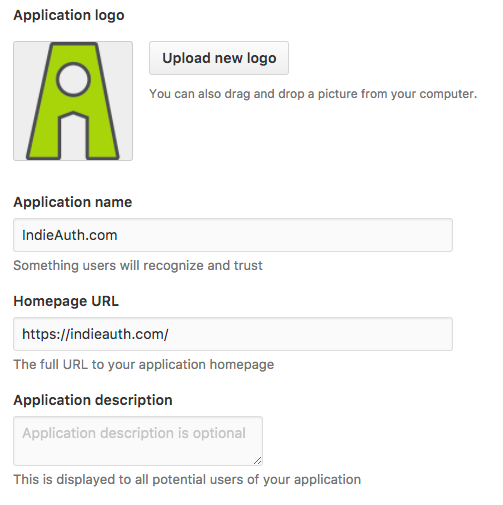
I tried adding a description of the application, hoping that it would appear on the GitHub OAuth screen, but sadly it did not! (I also reported that to GitHub, so I'll find out soon if it's a bug or if I'm misunderstanding their help text.)
After all that, the end result is that now when you sign in to something using IndieAuth.com with your GitHub account for the first time, you no longer see my face!
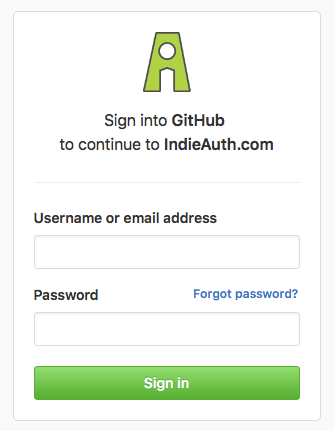
Hopefully this is much less shocking for people who are using this! I'm not a huge fan of the logo, although I do like the "clever" shape of the "A" with the negative space forming the "i". Maybe I just need to drop the outline. Perhaps that will be a future #100days project!
-
Check out this list I made: People who I didn't expect to see speaking at #Oktane16 @bjnovak https://li.st/aaronpk/people-who-i-didn-t-expect-to-see-speaking-at-oktane16-and-also-enjoy-their-talk-1qqvkMoYn0ULEE9VCjxh34

-
TIL Google is rolling out a new data center every month #oktane16
-
Just launched a big reorganization of https://oauth.net which should make it easier to find things! 🔒 #oauth2 #oktane16
-
@eyeficard Help! I can't connect my card to Flickr anymore! The auth screen pops up inside the app (which is bad OAuth practice) and now Yahoo rejects the request!

-
So you implemented an OAuth 2.0 API...

While OAuth 2.0 is a good framework for building an API, the spec itself leaves many things un-specified, and it's up to the implementer to make a decision based on their own security requirements. As such, most OAuth 2.0 implementations are not interoperable, which is often cited as a failure of OAuth 2.0. On the other hand, the current state of OAuth 2.0 implementations is that they are often similar enough that developers don't need to learn too many new concepts when dealing with them.
This post documents all the ways in which OAuth 2.0 implementations may differ. All implementations of OAuth 2.0 have made decisions about these things (whether intentional or not), otherwise they are incomplete implementations.
Every place in the spec that mentions things are a "MUST" are assumed to be implemented correctly. In other words, this does not ask you to verify that you implemented required parts of the framework correctly.
Client Registration (Section 2)
How do developers register a new client application?
- on a web page (link to registration page)
- programmatically (link to docs)
- other (please describe)
Aside from the client type and redirect URIs, what information is required or requested when registering an application?
- application name
- web page
- description
- logo image
- acceptance of legal terms
- other info:
Client ID (Section 2.2)
Clients should avoid making assumptions about the length of the client ID.
What is the maximum string length of client IDs issued?
Client Authentication (Section 2.3)
What form of client authentication is supported?
- Client ID and secret (this is the most common)
- Public/private key pair
- Other
Client Password (Section 2.3.1)
If clients are issued a
client_secret, which authentication mechanisms are supported for client identification:- HTTP
Authorizationheader (HTTP Basic Auth) - POST body parameters,
client_idandclient_secret(not recommended)
Other Client Authentication Methods (Section 2.3.2)
If clients are not issued a
client_secret, describe any other HTTP authentication schemes used to authenticate clients:Protocol Endpoints (Section 3)
Please specify the authorization endpoint and token endpoints. (note: this is only required here if your endpoints are specified in your documentation)
- Authorization endpoint:
- Token endpoint:
How do clients obtain the location of the authorization and token endpoints? The most common way is to specify them in the API documentation, although an automatic discovery method may be used instead.
- API Documentation
- Other method:
Authorization Endpoint (Section 3.1)
How does the authorization endpoint authenticate users? (e.g. requires username and password logins each visit? maintains session cookies?)
Response Types (Section 3.1.1)
Aside from "code" and "token", are any additional response types supported?
- Yes, additional types:
- No
Redirect Endpoint Confidentiality (Section 3.1.2.1)
- Are redirect endpoints required to be HTTPS? Yes No
- If HTTPS is not required, does the authorization endpoint warn users about the insecure redirect endpoint? Yes No
Redirect URI Registration (Section 3.1.2.2)
Registration of the redirect endpoints is required for public clients and clients using the "implicit" grant type. Aside from these uses, are all clients required to register redirect URIs?
- Are all clients required to register their redirect URIs? Yes No
- Is the registered redirect URI required to match exactly? Yes No
- If both previous answers are "no", does the authorization server support a variable query string component of the registered redirect URI? Yes No
- Can clients register multiple redirect URIs? Yes No
Note: if registration of redirect URIs is not required for all clients, then your authorization endpoint can be used by an attacker as an open redirector.
Invalid Redirect Endpoint (Section 3.1.2.4)
- Does the authorization endpoint inform the user that a given redirect endpoint is invalid?
Yes No
If the answer is "no", please describe what happens when an invalid redirect URI is provided in an authorization request. (The authorization endpoint must not redirect to this endpoint.)
Access Token Scope (Section 3.3)
- Is it possible for the authorization server to ignore (or add) scopes to the values requested during authorization? (For example, giving users the ability to not grant certain scopes requested by the application.) Yes No
- Does the authorization server document the default scope if none is specified during authorization? Yes (Documentation URL: ) No
Authorization Response (Section 4.1.2)
- What is the lifetime of authorization codes? (Maximum of 10 minutes is recommended)
- If an authorization code is used more than once, does the authorization server revoke all access tokens granted using the authorization code? Yes No
- What is the maximum size of authorization codes issued?
List any other parameters returned, as well as their maximum sizes:
Authorization Error Response (Section 4.1.2.1)
- If the request fails due to an invalid redirect URI or missing client ID, does the authorization server inform the user of the error? Yes No
- Does the error response contain an
error_descriptionfield with a human-readable description of the error that occurred? Yes No - Does the error response contain an
error_urifield which links to a human-readable web page about the error? Yes No
Implicit Grant (Section 4.2)
Implicit Grant Access Token Response (Section 4.2.2)
When does the access token response include an
expires_inparameter?- Always
- Sometimes
- Never
If the
expires_inparameter is not returned, the default value of the expiration is:Does the response always include the scope of the access token? (Optional if it's identical to the scope requested by the client.) Yes No
What is the maximum size of authorization codes issued?
List any other parameters returned, as well as their maximum sizes:
Authorization Error Response (Section 4.2.2.1)
- If the request fails due to an invalid redirect URI or missing client ID, does the authorization server inform the user of the error? Yes No
- Does the error response contain an
error_descriptionfield with a human-readable description of the error that occurred? Yes No - Does the error response contain an
error_urifield which links to a human-readable web page about the error? Yes No
Password Credentials Grant Type (Section 4.3)
Describe what types of clients can use the password credentials grant type:
Authorization Request (Section 4.3.1)
Describe how the user enters their credentials, e.g. a username and password prompt, client certificate auth, or whether the server uses or requires two-factor auth:
Access Token Request (Section 4.3.2)
Since the access token request involves sending the user's password to the authorization server, the server must protect against brute-force attacks. Describe what type of protection is used, e.g. rate limiting, sending alerts to the user, etc:
Access Token Response (Section 4.3.3)
- Does the client receives a refresh token when using the password credentials grant type? Yes No
Client Credentials Grant (Section 4.4)
What type of client authentication is used for the client credentials grant? e.g. client ID and secret, public key auth, etc.
- Client Credentials (client ID and secret)
- Others:
Can clients use the client credentials grant to request access to resources of other users who have been previously authorized? Yes No
If yes, describe how clients indicate which user they requesting an access token for. E.g. specifying a username, user ID, opaque token, etc.
Access Token Response (Section 4.4.3)
- Does the client receive a refresh token when using the client credentials grant type? (Not recommended) Yes No
Extension Grants (Section 4.5)
Authorization servers may support additional extension grant types such as SAML. List any additional grant types that are supported, along with links to their documentation.
Successful Access Token Response (Section 5.1)
- Does the access token response include an
expires_inparameter indicating the lifetime in seconds of the access token? Yes No - If not, what is the default value: , or describe another way the expiration time is indicated:
- Refresh tokens are returned for the following grant types:
- Authorization Code
- Implicit
- Client Credentials
- Refresh Token
- None of the above
- Describe any other conditions under which a refresh token is or is not returned when requesting an access token. E.g. only for specific clients, etc:
- What is the maximum size of access tokens issued?
- What is the maximum size of refresh tokens issued?
- List any other parameters returned, as well as their maximum sizes:
Error Response (Section 5.2)
- Does the error response contain an
error_descriptionfield with a human-readable description of the error that occurred? Yes No - Does the error response contain an
error_urifield which links to a human-readable web page about the error? Yes No
Refreshing an Access Token (Section 6)
- Does the authorization server issue new refresh tokens when a refresh token is used? Yes No
- If a new refresh token is issued, is the existing refresh token revoked? Yes No
Accessing Protected Resources (Section 7)
Describe how the resource server validates access tokens: (e.g. uses the authorization server's private API, shares cryptography keys, shares a database connection)
Describe how clients send the access token to the resource server. This typically involves sending the access token in the "Authorization" request header.
Access Token Type (Section 7.1)
Which access token types are accepted?
- Bearer tokens
- MAC tokens
- Others:
Error Response (Section 7.2)
Does the resource server inform the client of an error? Yes No
New Authentication Schemes
If you are using a new authentication scheme (other than Bearer tokens), there are several things to take into account when handling error responses. Please describe the following:
- How your new authentication scheme provides error status codes to the client
- What is the name of the error parameter? (e.g.
error) - Does your scheme also return an
error_descriptionparameter? Yes No - Does your scheme also return an
error_uriparameter? Yes No
Security Considerations (Section 10)
Client Authentication (Section 10.1)
- Are client passwords (or other credentials) issued to clients for specific devices? (e.g. an individual installation of an application on a device gets unique credentials.) Yes No
- When clients are unable to use authentication such as a
client_secret, does the authorization server employ other means to validate the client's identity?- Requires registration of redirect URIs for clients
- Involves the user in confirming the client's identity
- Other:
- No
Client Impersonation (Section 10.2)
- Does the authorization server provide the user with information about the client? Yes No
- ... about the requested scope? Yes No
- ... and lifetime of the request? Yes No
- Describe the security measures taken to ensure repeated authorization requests come from the original client and not an impersonator:
-
A Little Twitter Developer History
Back in the early days of Twitter, I noticed that several tweets I was seeing showed "via _____" next to the date, which linked to the application that was used to post the tweet. I thought "hey that's a clever way to give credit to applications" and thought it would be a good way to get people to discover the Twitter app I was creating at the time.
Of course since Twitter was still so new, there was no automatic way for this to happen. I managed to track down an email posted to the "Twitter Development Talk" mailing list where someone was asking how to do this.
Date: Wed, 24 Oct 2007 22:39:29 -0000 From: "Ricky" <[email protected]> To: Twitter Development Talk <[email protected]> Subject: How do you set the source from the API I am trying to update a status of a user via the methods on the API. I managed to update my status but it always says updated from web. I've seen other people update from facebook or whatever so I was wondering if there is a way that I can customise this label. ... Anything I can change to set the source here? Cheers
Al3x, one of the first engineers at Twitter (who was primarily focusing on building the developer platform), replied to the list:
Date: Wed, 24 Oct 2007 15:43:14 -0700 From: "Alex Payne" <[email protected]> To: [email protected] Subject: Re: How do you set the source from the API Please email me off-list and I'll set you up with a source link. Thanks. -- Alex Payne http://twitter.com/al3x
I thought "that sounds like something I can do," and proceeded to have the following email exchange with Al3x.
Date: Wed, 28 Nov 2007 20:43:30 -0800 From: "Aaron Parecki" <[email protected]> To: [email protected] Subject: custom api status Hi Al3x, I happened across this page: http://groups.google.com/group/twitter-development-talk/browse_thread/thread/e62039d65648614b and noticed you were asking people to contact you to set up a custom source link. Could you please set me up with "untied"? Thanks! Aaron Parecki
Date: Thu, 29 Nov 2007 11:33:59 -0800 From: "Alex Payne" <[email protected]> To: "Aaron Parecki" <[email protected]> Subject: Re: custom api status Do you have a link for your application? -- Alex Payne http://twitter.com/al3x
Date: Thu, 29 Nov 2007 11:35:25 -0800 From: "Aaron Parecki" <[email protected]> To: "Alex Payne" <[email protected]> Subject: Re: custom api status It is still in progress. http://untied.us Aaron
Date: Thu, 29 Nov 2007 11:38:39 -0800 From: "Alex Payne" <[email protected]> To: "Aaron Parecki" <[email protected]> Subject: Re: custom api status Alright. Please start sending a parameter named "source" with a value of "untied" when you POST updates to our API. I'll push out the change today. -- Alex Payne http://twitter.com/al3x
Date: Thu, 29 Nov 2007 11:46:00 -0800 From: "Aaron Parecki" <[email protected]> To: "Alex Payne" <[email protected]> Subject: Re: custom api status thanks!
The things I found amusing from this were:
- this was an undocumented feature that Twitter was apparently not opposed to people using
- it required a manual change on Twitter's end that required "pushing out" the change



















